All products are independently selected by our experts. To help us provide free unbiased advice, we’ll earn an associated commission if you buy something. Click here to learn more
One of the largest databases of passwords ever discoveredhas appeared on the Internet, security researchers have warned. A large amount of stolen login credentials — with an estimated 9,948,575,739 unique passwords stored in plain text — was posted on a popular hacker forum late last week.
Called RockYou2024.txt, the file is filled with stolen passwords that could unleash “a cascade of data breaches, financial fraud and identity theft,” according to experts at CyberNews, who first discovered the database shared by a forum user known only by the pseudonym ObamaCare.
It appears that the database is a mix of old and new data breaches.
“Essentially, the RockYou2024 leak is a compilation of real-world passwords used by individuals around the world. Revealing that many passwords to threat actors significantly increases the risk of credential stuffing attacks,” the researchers said.
Credential stuffing is a popular form of attack that sees hackers use stolen login details from one website to attempt to login to another. If you reuse the same username and password for many services, websites and applications, then you will be susceptible to this type of cyber attack.
A recent wave of attacks against Santander, Ticketmaster and QuoteWizard are widely believed to be the direct result of credential stuffing attacks by victims of cloud service provider Snowflake.
And now the team at CyberNews believes the same could happen to the latest database, warning: “Threat actors could exploit RockYou2024’s password compilation to carry out brute-force attacks and gain access to unauthorized access to various online accounts used by individuals using passwords contained in the data records.”
The database of stolen passwords was shared on a popular hacking forum by someone with the username ObamaCare. Experts have verified that the text file contains millions of passwords, based on the dataset originally released on the same forum three years ago
CYBERNEWS PRESS OFFICE
RockYou2024.txt is based on an earlier leak, RockYou2021.txt, shared by hackers online three years ago.
At the time, that text file filled with stolen usernames, email addresses and matching passwords was the largest set of stolen data of all time. – a record that has since been broken by a leak that researchers refer to as the “mother of all breaches”. Since the launch of RockYou2021.txt, approximately 1.5 billion passwords have been added to the database, putting millions more people at risk of attack.
There is no easy solution for anyone whose passwords are included in the RockYou2024.txt database.
However, the CyberNews team has shared some tips for those who want to protect themselves from credential stuffing or other types of post-breach attacks:
- Immediately reset passwords for everything accounts that rely on a password included in the database
- Create a unique alphanumeric password for each online account
- Turn on multi-factor authentication, like a one-time code sent to your phone number, to protect accounts
- Use a password manager to store and manage complex passwords
- Use tools like haveibeenpwned.com/ to check if your data has been breached
Astounding Database of Cracked Passwords Just Coming a few days after new research from Kaspersky has demonstrated that millions of popular passwords can be cracked in less than a minute, thanks to improvements in computer hardware and smarter AI-powered algorithms to break into online accounts.
According to data from Kaspersky, hackers tried to crack passwords 32 million times last year alone. This figure is likely to increase as it becomes easier and easier to brute force passwords with the latest algorithm and hardware.
Kaspersky researchers used a combination of the latest algorithms and a Nvidia RTX 4090 £1,549 GPU to attempt to crack the database of 193 million passwords discovered on the Dark Web. All stored passwords were hashed and salted – meaning the researchers still had to guess them correctly to get in.
If your password is 8 characters or less, it can be cracked in just 17 seconds, researchers found. Most of these passwords were all lowercase or uppercase English letters with a few numeric digits – showing the importance of using special characters, such as symbols, to make your password harder to crack.
In total, 45% of all passwords analyzed by the database – 87 million – could be guessed within a minute.
Most of the passwords examined by the researchers contained at least one word from the dictionary, which significantly reduces the strength of a password and makes it more susceptible to brute force-style attacks.
As researchers cracked millions of passwords, certain patterns began to emerge. If you want to create a strong, unique password to protect your account, avoid some of these popular patterns –
Popular word
- forever
- love
- hacker
- gamer
Common names
- Daniel
- kevin
- Ahmed
- nguyen
- gambling
Standard passwords
- the password
- qwerty12345
- admin
- 12345
- Team
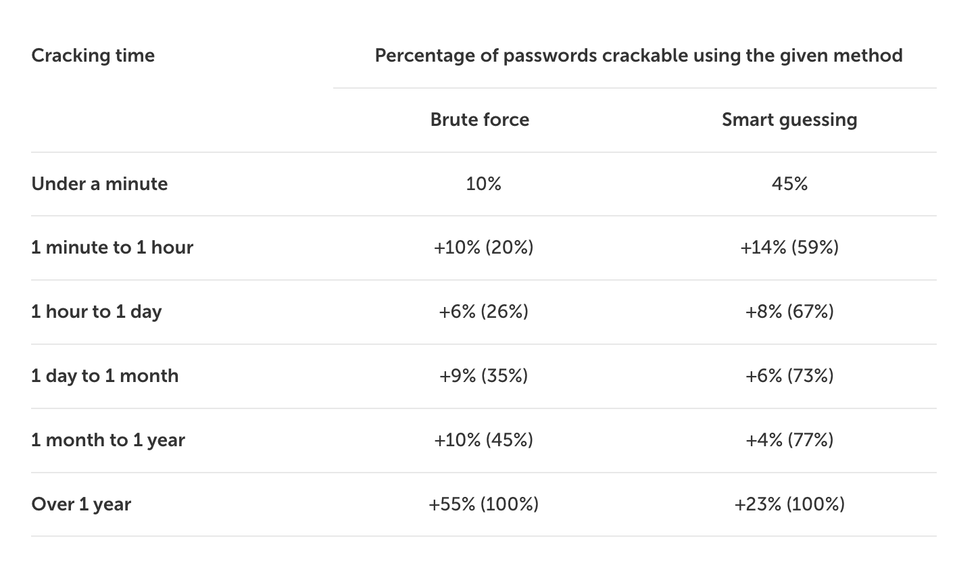
Kaspersky analyzed millions of hashed-and-salted passwords shared by hackers on the Dark Web to find out how long it would take to crack accounts
KASPERSKY
Kaspersky used a brute-force algorithm to achieve these results, a technique that LOT popular with hackers. This tries all possible password combinations by going through a list of words from the dictionary as well as different types of characters, numbers and more.
The researchers tried to improve on the initial results by programming the algorithm to consider combinations of known characters, common names and sequences.
Hackers have also developed clever algorithms that try to replace characters, such as replacing an “a” with “@” or an “e” with “3” – so don’t do this when creating a password, you won’t make your account more secure.
With the most efficient brute force algorithm, the researchers were able to crack 59% of 193 million passwords within an hour and almost three-quarters of all passwords (73%) within a month.
Only 23% of passwords from the Dark Web database would take more than a year to crack.
Discussing their findings, security experts from Kaspersky noted: “Unconsciously, human beings create ‘human’ passwords – containing words from the dictionary in their native languages, with names, numbers, ETC.things that our busy brains are easy to remember easily.
“Even seemingly strong combinations are rarely completely random, so they can be guessed by algorithms. With this in mind, the most reliable solution is to create a completely random password using modern and reliable password managers.”
Passkeys are an increasingly common solution to protect your accounts without relying on a long alpha-numeric password that is impossible to remember. This smart solution uses the security feature built into your smartphone—like Face ID recognition on the iPhone, fingerprint scanners on the Samsung Galaxy, and more—to verify your identity when you sign in to a website or app.
Support for these password replacements is slowly being adopted by larger web services and applications, with Elon Musk enables X support for iPhone owners at the beginning of this year, with WhatsApp also supports passkeys to avoid its users relying on guessable passwords.
Password managers are another popular solution.
These standalone apps generate unique passwords without any discernible patterns – and a healthy mix of lowercase and uppercase characters, symbols, numbers, and more. It would be impossible to memorize these long and unique jumbles of characters ANY sign in, so password managers encode and store it all for you – filling in fields within apps and websites for you.
You’ll only need to remember one password: the one that unlocks your password manager.
Password managers, like 1Password (pictured), can manage long, unique alphanumeric passwords for every online account and monitor the Dark Web for breaches and hacks
1APOLOGY PRESS OFFICE
Many of these apps also rely on biometrics, like fingerprints and face scans, to lock everything down.
Apple includes a password manager – known as iCloud Keychain — as part of the mobile operating system that ships with every iPhone, iPad and Mac, while Californian rival Google has built a similar system into Chrome. However, the iPhone manufacturer has big plans to overhaul this system with a real competitor like 1Password, NordPass and LastPass in the coming months as part of the next free upgrade.
RECENT DEVELOPMENTS
In recent months, we have seen Security researchers uncover so-called ‘mother of all breaches’, with billions of usernames and passwords stolen for popular sites like LinkedIn, X (formerly Twitter), Telegram and Dropbox. Not only that, but hackers used credential stuffing to breach half a million Roku accounts and spend money using saved payment details.
Whatever you do, be sure not to use a password on this list published by Nord.